Modular blockchains for Intermediates
The Future of Scalable, Efficient Systems
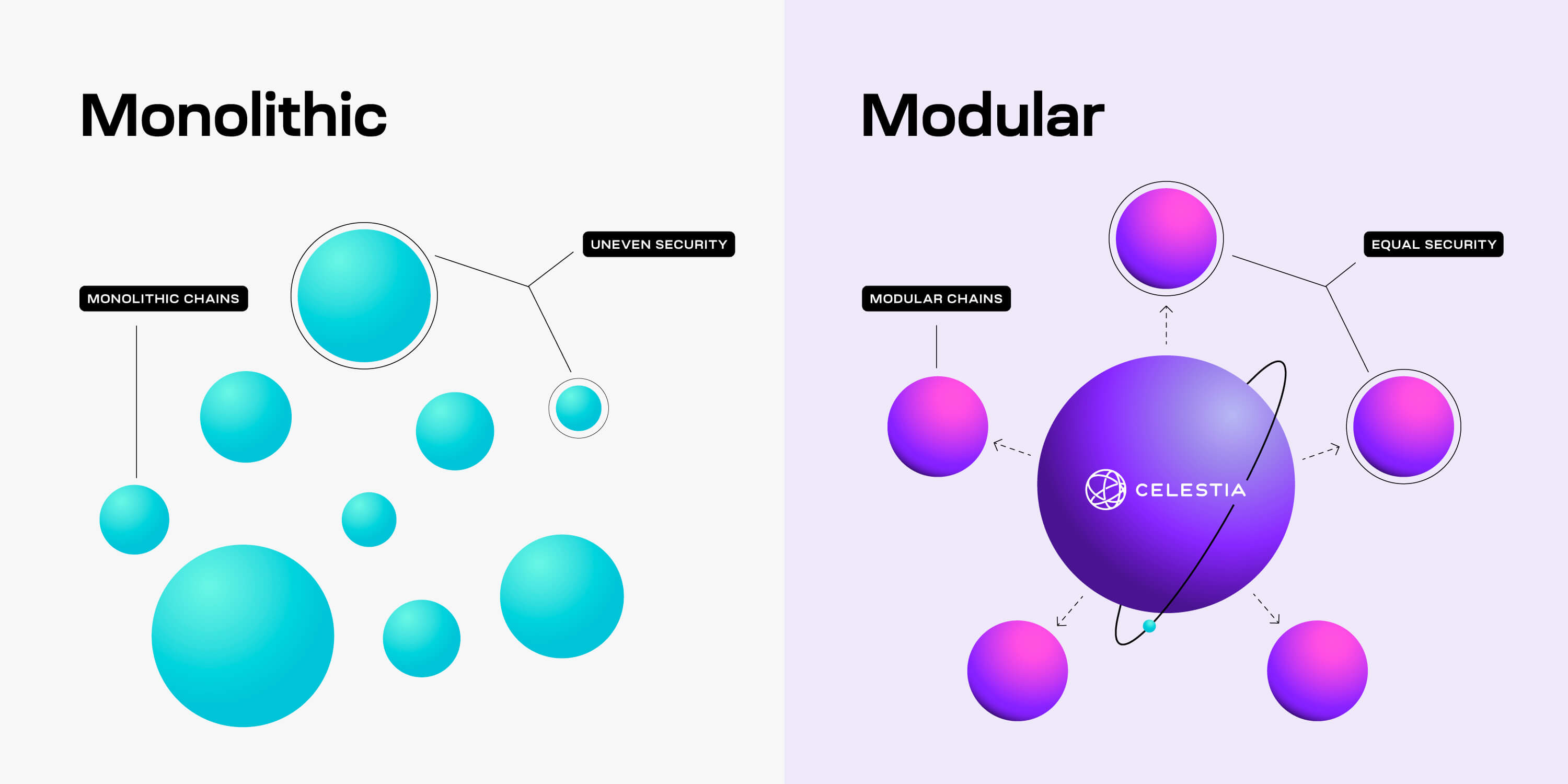
Modular blockchains enhance scalability and efficiency by dividing tasks among specialized layers, unlike monolithic chains that handle everything. This approach promises better performance for a large number of users.
Scalability
Remember, a core idea of modular blockchains is that they separate functions across multiple chains. This concept also brings extra scalability. A modular L1 like Celestia can now specialize in data availability. Without smart contracts, the L1 can focus all its resources on providing data for L2s, like rollups. Specialization is key because more data the L1 can provide allows rollups to process more transactions.
As for transactions, in the monolithic world, all apps live on the same chain. The downside is that users of different applications all have to compete to get their transactions processed. In the modular paradigm, apps live on separate chains. This means that a user of one app isn’t competing with the users of a different app for computation. So, transactions for many different apps can get processed at the same time.
Sovereignty
When an app is built on a shared monolithic blockchain, it is bound by predetermined rules. The rules might be around social consensus (when it's okay to hard fork) or around technical rules (what programming languages you can write smart contracts in).
Modular blockchains enable control over the rules of an application through sovereignty. Developers can make changes to the tech stack without permission from outside applications. For example, they could make a more performant execution environment or change how transaction processing works - who wants parallel transactions?
Importantly, sovereignty gives independence. Developers and the community can freely set the rules for their sovereign chain that aligns with their app and community’s ethos. It is sovereignty that places autonomy back in the hands of the community.